Vulnerabilities in Single Sign-On services could be abused to bypass authentication controls | The Daily Swig

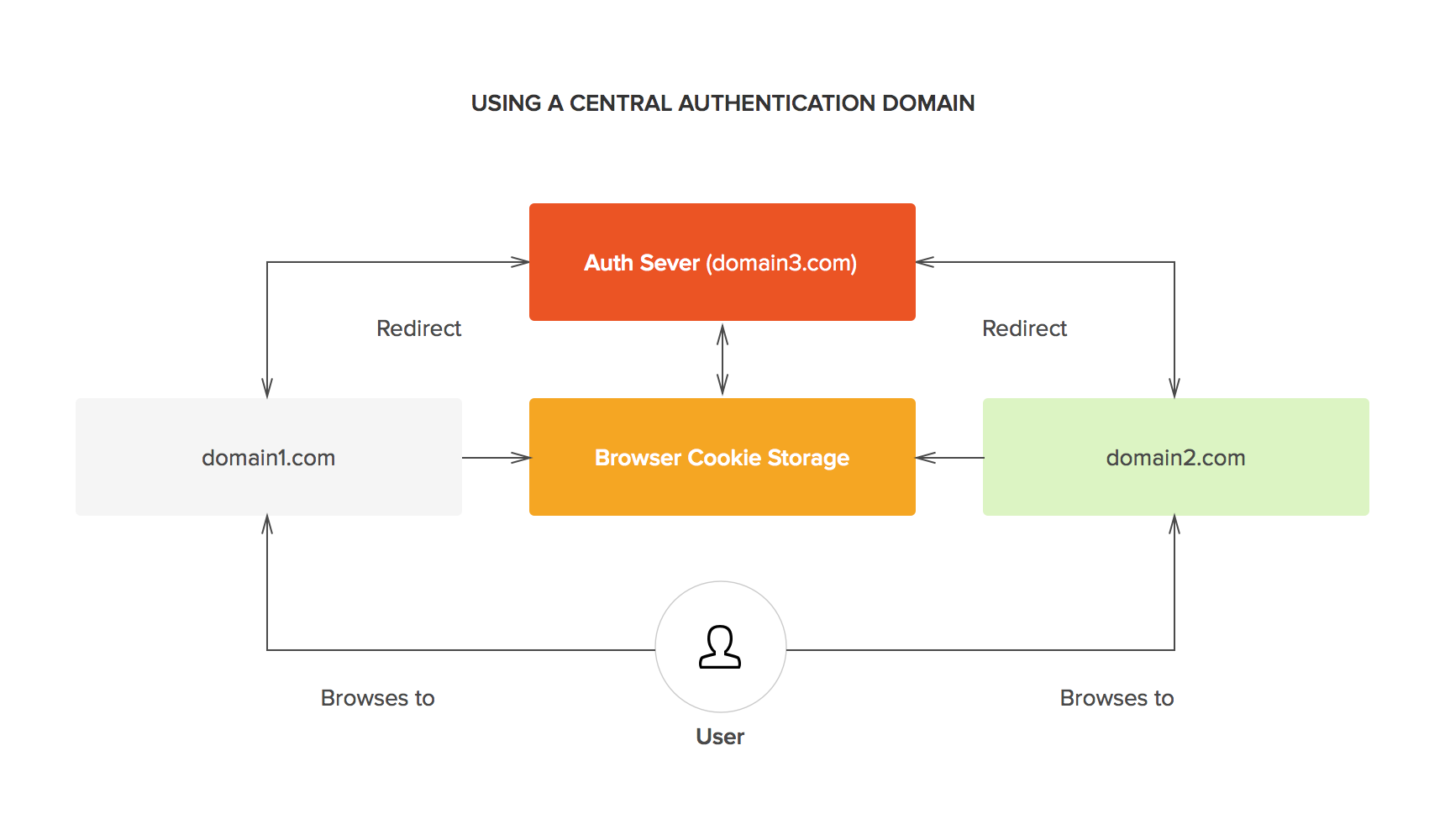
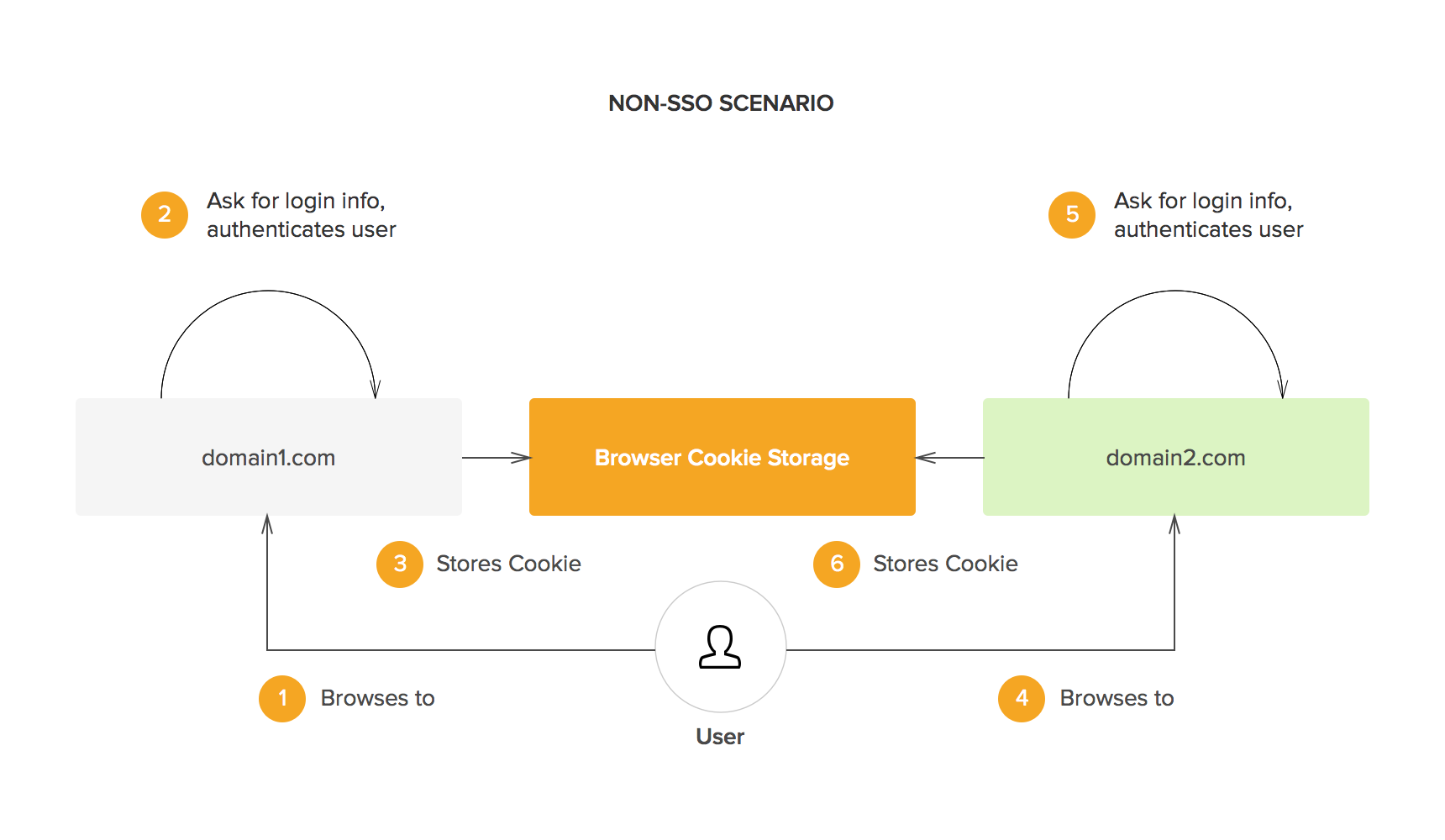
Single Sign-On(SSO) -SAML Authentication Explained | by Prakhar Jain | Connected Lab TechBlog | Medium

SAML web-based authentication for Security (Single Sign-On SSO) | by Kubernetes Advocate | AVM Consulting Blog | Medium