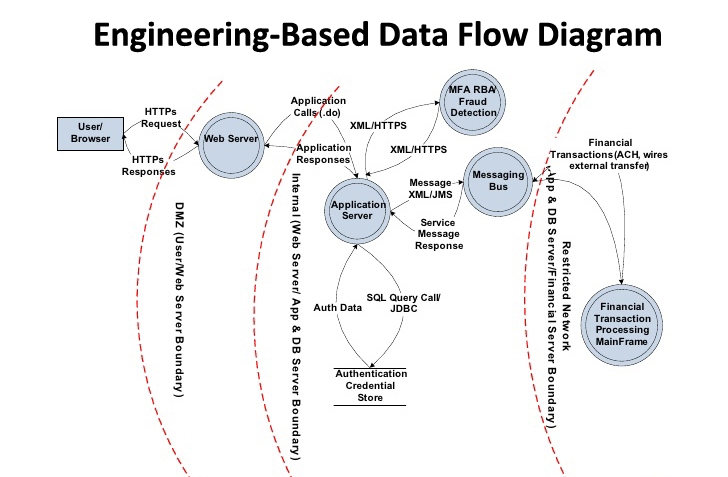
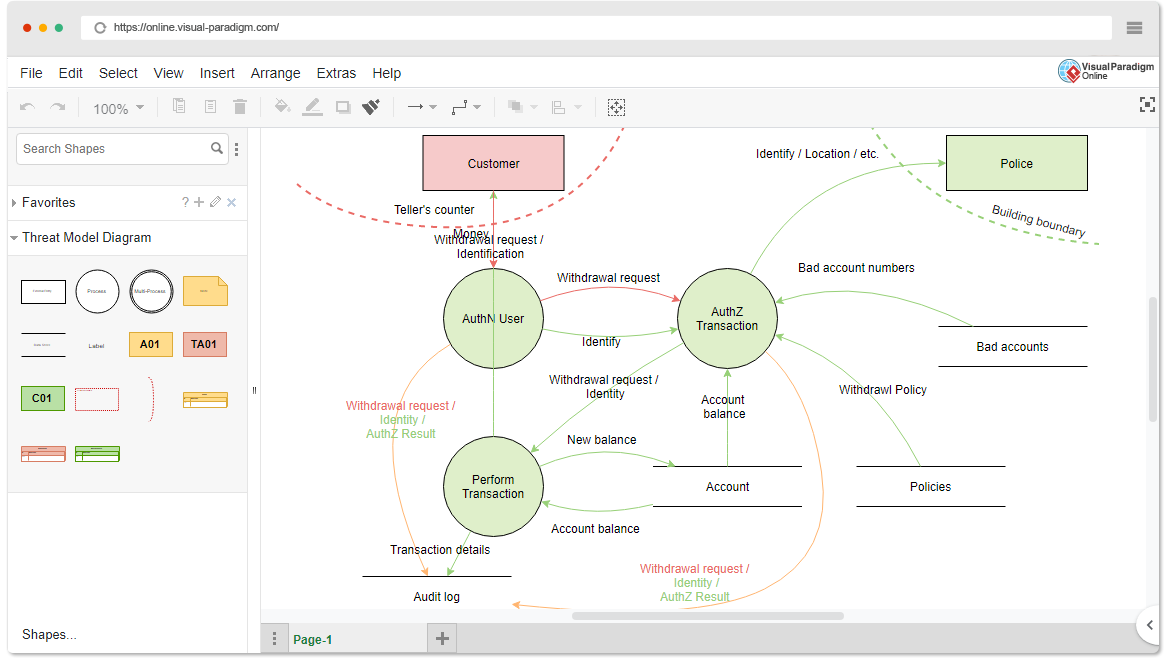
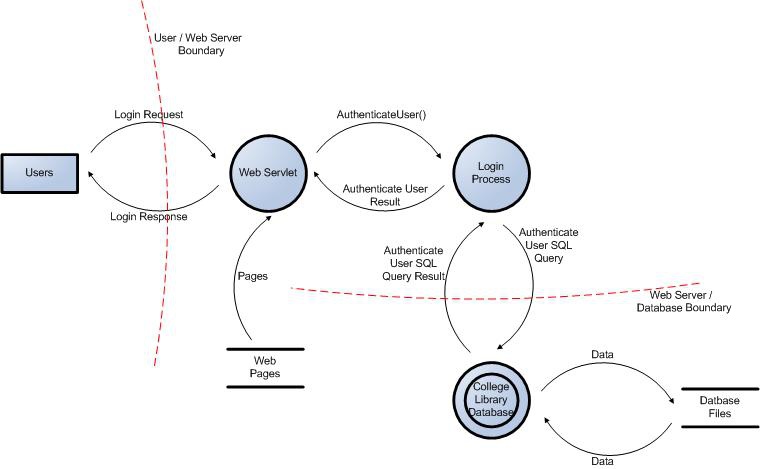
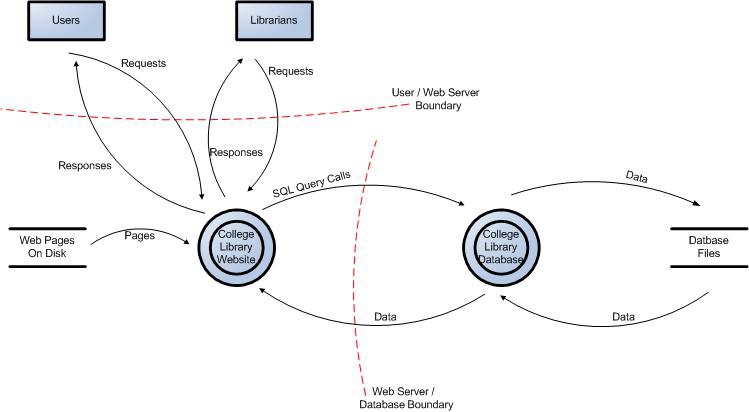
![PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b1ef84599ca7a255bbf98822e25970d69ad49dac/4-Figure1-1.png)
PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar
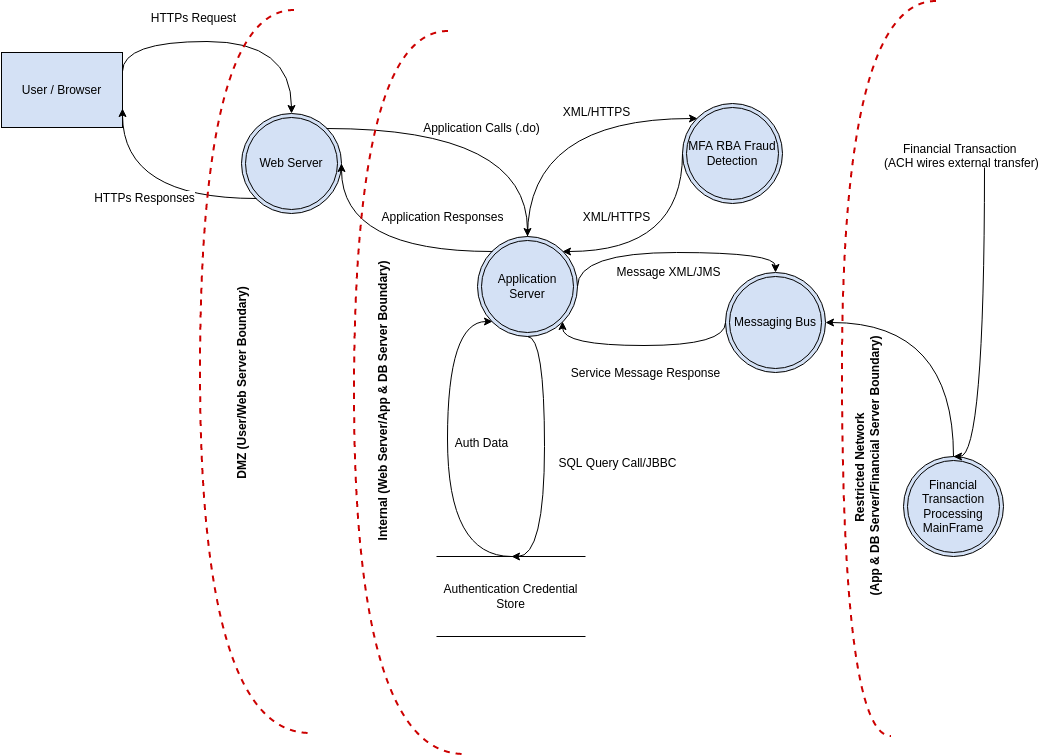
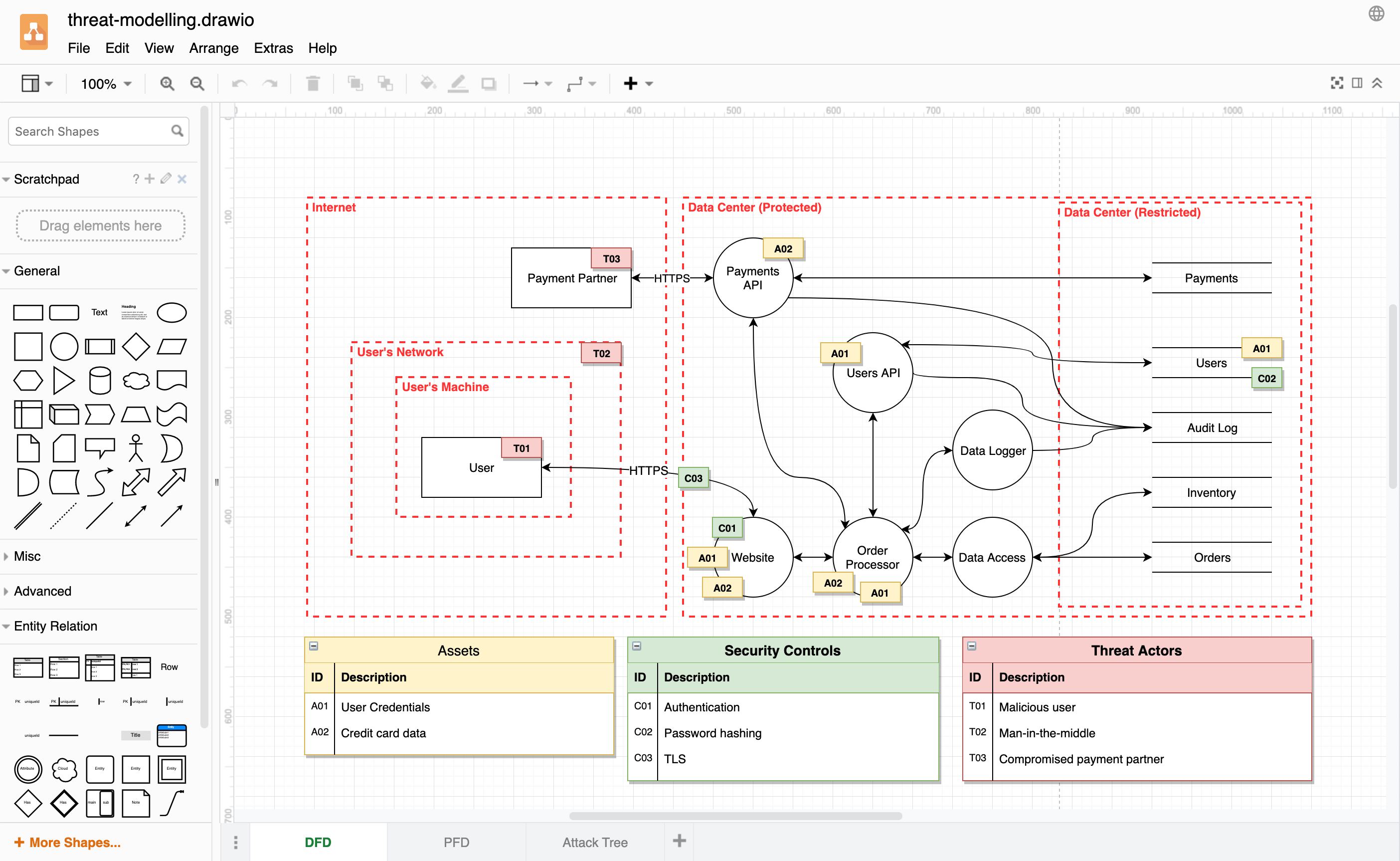
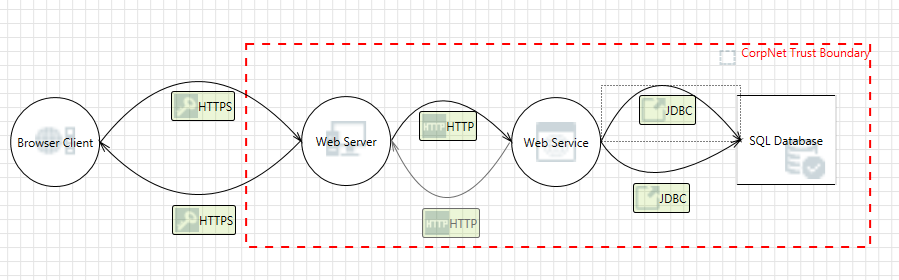
![Threat modeling OpenID Connect, OAuth 2.0 for beginners using OWASP Threat Dragon [Part 2] | by Tanvir Ahmed | FAUN Publication Threat modeling OpenID Connect, OAuth 2.0 for beginners using OWASP Threat Dragon [Part 2] | by Tanvir Ahmed | FAUN Publication](https://miro.medium.com/max/655/1*h1u_qXi3Np3kYu_eqG3hFw.jpeg)
Threat modeling OpenID Connect, OAuth 2.0 for beginners using OWASP Threat Dragon [Part 2] | by Tanvir Ahmed | FAUN Publication

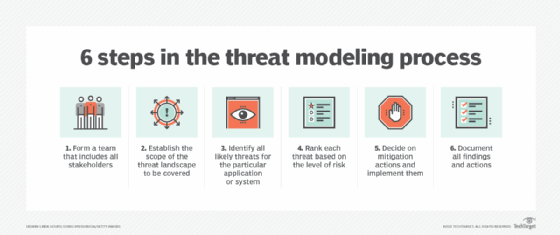
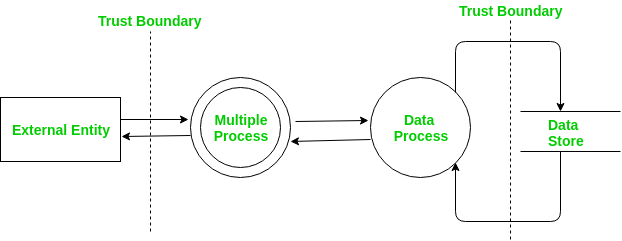
Threat modelling connected and autonomous vehicle cybersecurity: an overview of available tools – Secure-CAV
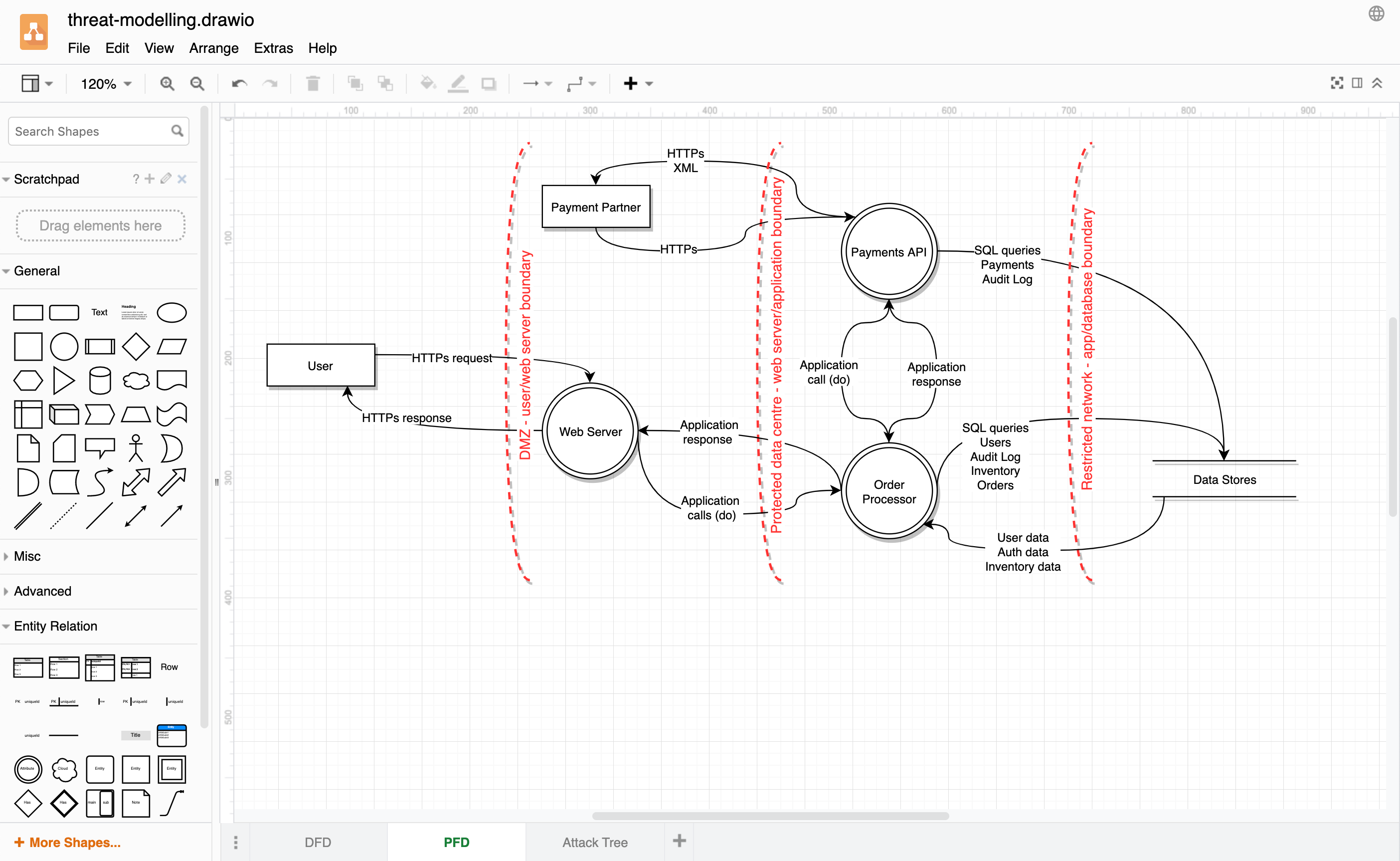
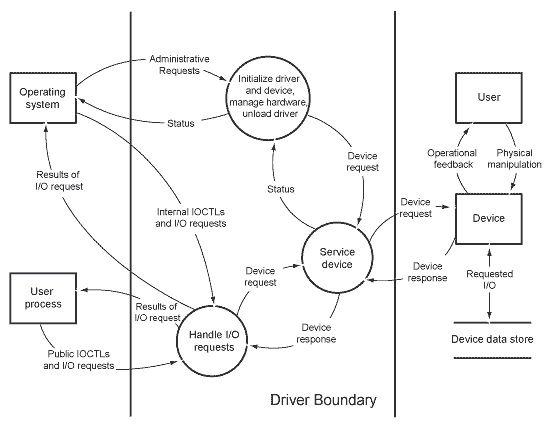
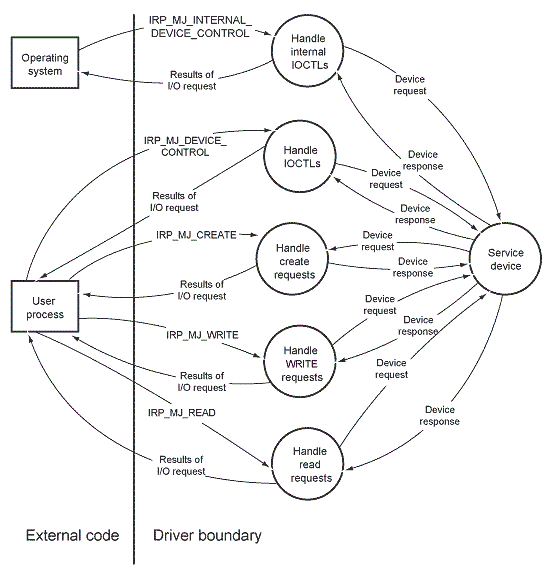
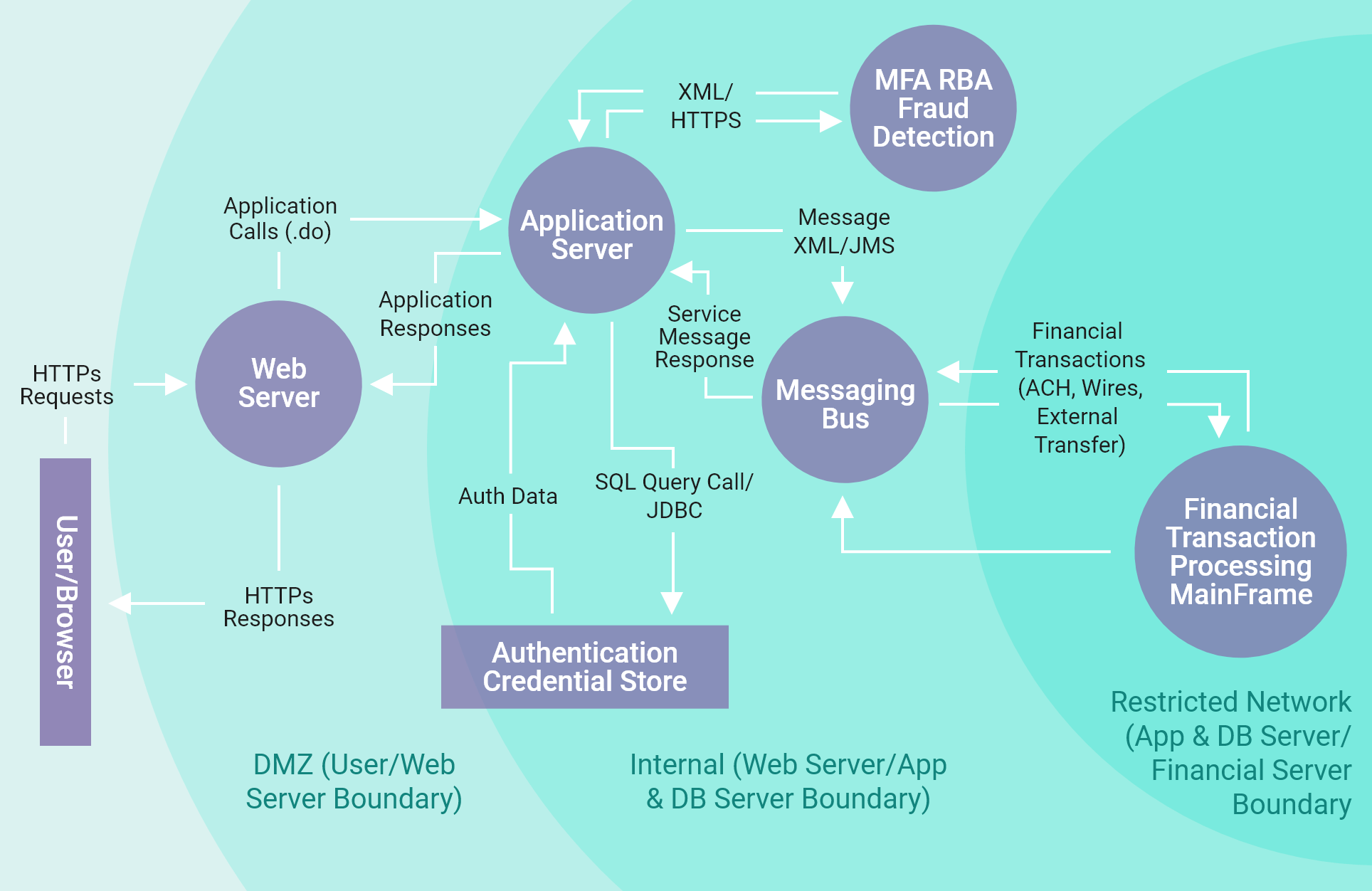
![PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar PDF] Checking threat modeling data flow diagrams for implementation conformance and security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b1ef84599ca7a255bbf98822e25970d69ad49dac/11-Figure6-1.png)