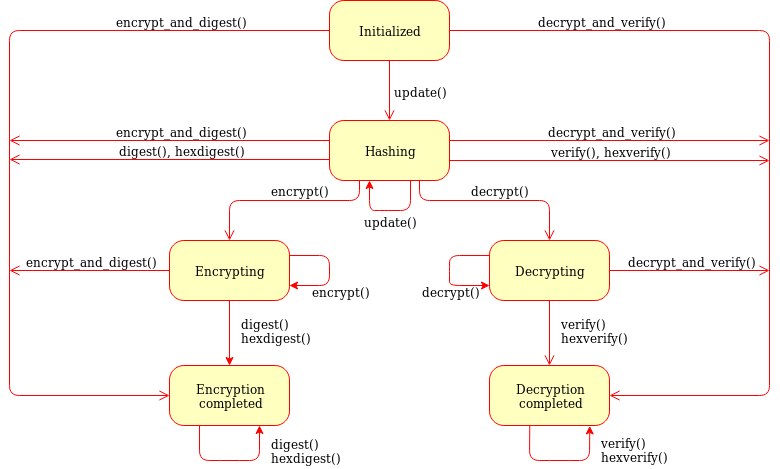
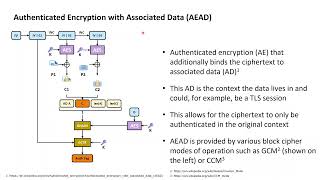
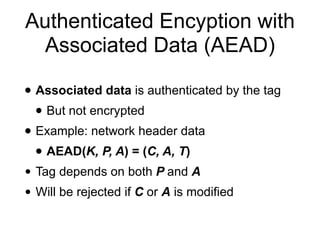
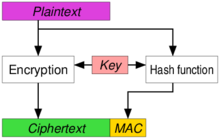
TLS 1.3 (with AEAD) and TLS 1.2 cipher suites demystified: how to pick your ciphers wisely - Cloud Insidr

Basic block design of an AEAD, where ciphertext and authentication tag... | Download Scientific Diagram

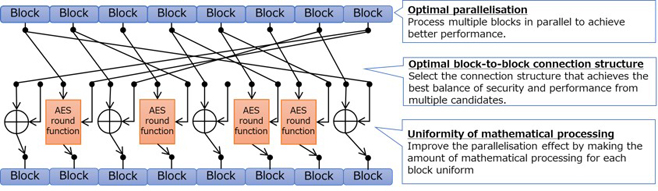
A list of lightweight authenticated encryption with associated data... | Download Scientific Diagram
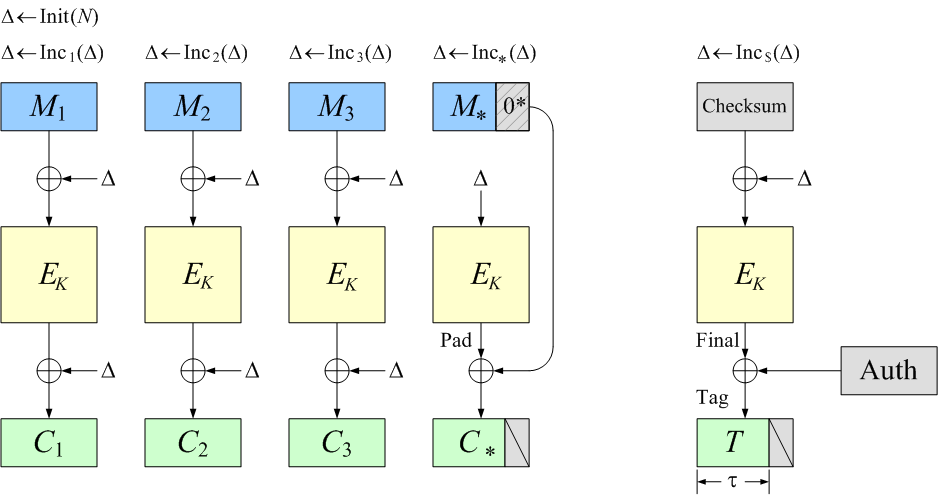
![PDF] Lightweight Authenticated Encryption Mode of Operation for Tweakable Block Ciphers | Semantic Scholar PDF] Lightweight Authenticated Encryption Mode of Operation for Tweakable Block Ciphers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/825967c542f0b3d236ab5003305bd56fb9c3b44c/2-Table1-1.png)
PDF] Lightweight Authenticated Encryption Mode of Operation for Tweakable Block Ciphers | Semantic Scholar

Exploring Authenticated Encryption with Associated Data - EngineerZone Spotlight - EZ Blogs - EngineerZone
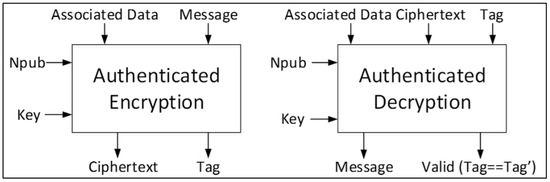
Cryptography | Free Full-Text | Comparison of Cost of Protection against Differential Power Analysis of Selected Authenticated Ciphers | HTML